DHCP Snooping
Overview
Suppose that an attacker could bring up a rogue DHCP server on a machine in the same subnet as that same client PC. Now when the client broadcasts its DHCP request, the rogue server could send a carefully crafted DHCP reply with its own IP address substituted as the default gateway. This is called DHCP Snooping.
Cisco Catalyst switches can use the DHCP snooping feature to help mitigate this type of attack. When DHCP snooping is enabled, switch ports are categorized as trusted or untrusted. Legitimate DHCP servers can be found on trusted ports, whereas all other hosts sit behind untrusted ports.
Example
SW11(config)#ip dhcp snooping vlan 1
SW1(config)#ip dhcp snooping
SW1(config)# int e0/1
SW1(config-if)# ip dhcp snooping trust
SW1(config-if)# ip dhcp snooping limit rate 25
SW1#sh ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
AA:BB:CC:00:03:00 192.168.0.2 86351 dhcp-snooping 1 Ethernet3/3
Total number of bindings: 1
http://packetpushers.net/ccnp-studies-configuring-dhcp-snooping/
Option 82
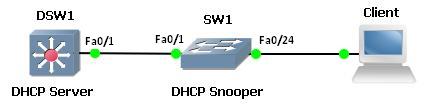
Option 82 is used by the DHCP snooper to add information related to the request so the DHCP snooper can compare the reply with the information to ensure this reply can be trust.
However, this feature can cause some problems in certain ways. For a topoloty like the image above, SW1 will add option 82 into the DHCP request by default if DHCP snooping is enabled. DSW1 will drop it by default because of the option. That will cause DHCP request failed.
Solution 1
SW1(config)#no ip dhcp snooping information option
Solution 2
DSW1(config)#ip dhcp relay information trust-all
Note
If there is one more switch in the topology, the switch can allow
SW2(config)#ip dhcp snooping information option allow-untrusted